Search Knowledge Base by Keyword
UKHost4u SSH Gate Outline
Secure Shell or SSH is a specified method used to link to a distant container and carry out the necessary commands on it. SSH commands are encrypted and protected; a digital certificate is used to validate the client/server connection. Also, the password is secured by being encrypted.
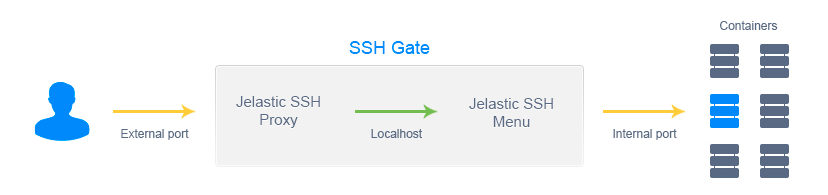
In UKHost4u, SSH access is made available by adding a new infrastructure component to the core, known as SSH Gate. SSH Gate obtains the users’ connections from the internet and then passes on these connections to the preferred container with the help of an internal network.
There are two independent parts of the authentication process in the UKHost4u SSH Gate:
- Connection from client to Gate known as external authentication
- Connection from Gate to users’ container known as internal authentication
The above-mentioned parts of the authentication process are dependent on a standard SSH protocol with the help of private or public keypairs.
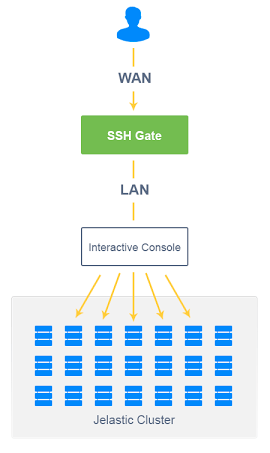
You can easily access the following with UKHost4u SSH Gate:
- The whole account is where you can move across the environments and containers with the help of a communicative menu without additional validation.
- Separate contains straight away while using them remotely using extra tools or SFTP and Fish protocols.

While retrieving the containers through SSH, a user gets all the needed information and can also manage the prime services with the following type of sudo commands;
sudo /etc/init.d/jetty start
sudo /etc/init.d/mysql stop
sudo /etc/init.d/tomcat restart
sudo /etc/init.d/memcached status
sudo /etc/init.d/mongod reload
sudo /etc/init.d/nginx upgrade
sudo /etc/init.d/httpd help
Additionally, you get the support of SFTP or Secure File Transfer Protocol at our platform by executing the stringed daemon for SFTP connections handling. It allows you to access, handle, and transfer files straight to the container through SSH Gate, and in such a way, assures protection.
FISH or Files transferred over Shell Protocol is another protective network protocol. It is empowered by certain famous FTP users and file managers. It also lets you safely access and manage a container’s file system.
