Search Knowledge Base by Keyword
How To Whitelist An IP Address In WHM
Web Hosting Manager (WHM), developed by cPanel, serves as a server-based management interface. It enables administrators to grant users access to cPanel, allowing them to effectively manage their web hosting environment. Among the most commonly used firewalls on cPanel is ConfigServer Security & Firewall.
Whitelisting an IP address involves the firewall including the IP address in the list of allowed entries (often within the iptables or firewalld service). This action ensures that the firewall refrains from obstructing the specified IP address for any cause. Such a step might be essential for enabling server access via SSH or for averting IP restrictions prompted by email problems. However, it is crucial to exercise extreme caution when utilising this approach.
Steps for Whitelisting
Below are the steps to whitelist an IP address in WHM –
1. Ensure you access the WHM control panel using correct login credentials. Typically, WHM can be reached through your domain at “/whm” or by utilizing port 2086 / 2087.
2. Head to ConfigServer Security & Firewall, located within the plugins section at the lower part of cPanel’s left-hand menu.
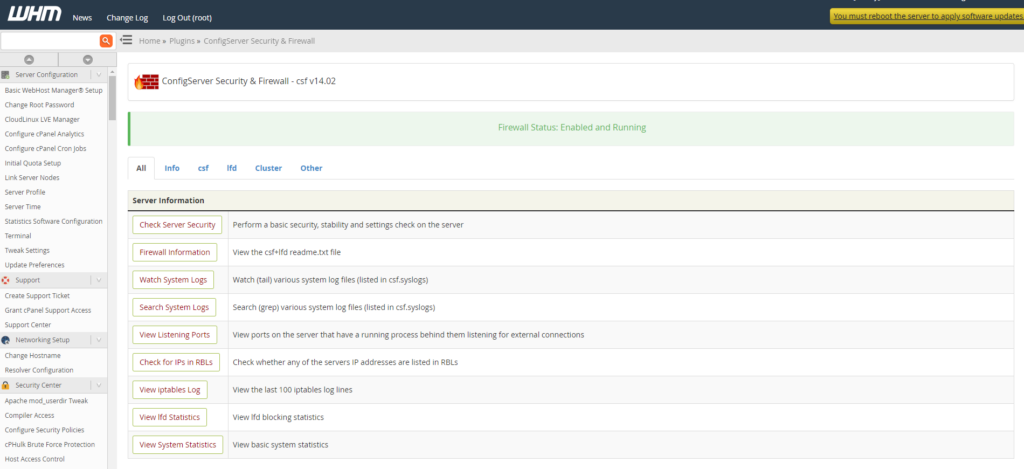
3. At this point, the user will encounter the firewall management screen.
4. Presently, the user has the option to scroll down to “csf – Quick Actions” and input the IP address to be whitelisted in the Quick Allow field.
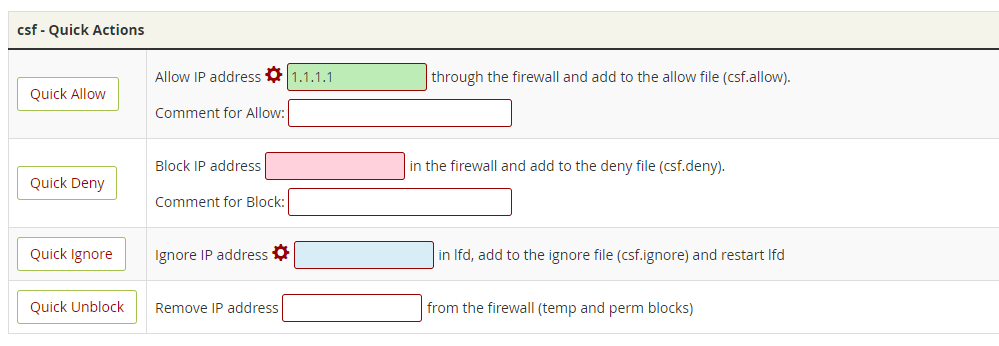
5.
Ultimately, click on Quick Allow to complete the process of adding the IP address to the firewall whitelist.
Words of advice
Whitelisting, despite its advantages, can present significant security risks that require careful consideration. When an IP address is added to the whitelist, it gains unrestricted access to the system, services, or applications covered by the whitelist. While this can be advantageous for allowing specific users or devices to function seamlessly, it also introduces potential vulnerabilities that malicious actors could exploit.
One notable risk is the potential for insider threats. If a legitimate user’s device becomes compromised, the attacker could potentially use that device’s trusted IP address to gain unauthorised access. This is particularly concerning if the compromised device has elevated privileges or access to sensitive data.
Additionally, the static nature of whitelists can be a drawback. IP addresses can be spoofed or manipulated, allowing attackers to imitate trusted addresses and potentially breach the system. Moreover, if an attacker manages to gain control over an IP address that’s on the whitelist, they can bypass security measures without raising suspicion.
Furthermore, maintaining and managing a whitelist can become cumbersome, especially in large-scale environments. As the number of allowed IP addresses grows, it becomes increasingly difficult to monitor and update the list effectively. This could lead to oversight, outdated entries, and potential security gaps.
In summary, while whitelisting can be a useful tool for granting authorised access, its static nature and potential for abuse underscore the importance of implementing additional security layers. Combining whitelisting with other security measures, such as regular updates, monitoring for unusual activity, and multi-factor authentication, can help mitigate the associated risks and create a more robust security posture.
